二进制安全 [2023]一些特殊指令不触发单步 ```cpp SGDT, SIDT, SLDT, SMSW, STR ``` 您观察到的行为与现代 x86 处理器中的用户模式指令预防 (UMIP) 功能有关。UMIP 是一项安全功能,可防止处理器处于用户模式时执行某些特权指令。这些指令包括SGDT、SIDT、SLDT、SMSW 和 STR。 当这些指令在用户模式下执行时,它们不会触发单步陷阱,并且陷阱标志 (TF) 将保持设置状态,正如您所注意到的。这是启用 UMIP 时的预期行为 (CR4.UMIP = 1)。UMIP 旨在防止用户模式代码操纵或访问敏感系统信息。 UMIP 对于安全目的很有用,因为它限制在用户模式下执行潜在危险的指令。然而,对于使用单步调试和分析的逆向工程师和安全研究人员来说,这可能是一个挑战。 阅读全文 2023-11-10 huoji 0 条评论
APT研究二进制安全渗透复现 [2023]我是如何通过EDR在五分钟内发现完全未标记的威胁 > 在日常EDR运维中,我们发现了一个异常的情况,但是无法立刻确定,因为所有已知的数据库都无法匹配上这个异常情况..... # 开始 在日常运维中,我们发现了EDR很少会报告可疑的活动,这个行为除了少部分流氓软件以外,一般是不会出现在一个完全未知的程序上: 阅读全文 2023-11-07 huoji 3 条评论
APT研究系统安全二进制安全 [2023]How did I discover a completely unmarked threat within five minutes through EDR > In daily EDR operation and maintenance, we have discovered an abnormal situation, but we cannot immediately determine it because all known databases cannot match this abnormal situation # At the Begin In daily operations and maintenance, we have found that EDR rarely reports suspicious activities, which generally do not occur on a completely unknown program except for a few rogue software: 阅读全文 2023-11-02 huoji 0 条评论
二进制安全 [2023]给火绒接了云查 作为火绒的忠实粉丝,常常感觉它力不从心,也不想换卡巴斯基,毕竟火绒老粉丝了,考虑到骇人的查杀率,给他接了个卡巴斯基的KSN云查,云查前:  云查后: 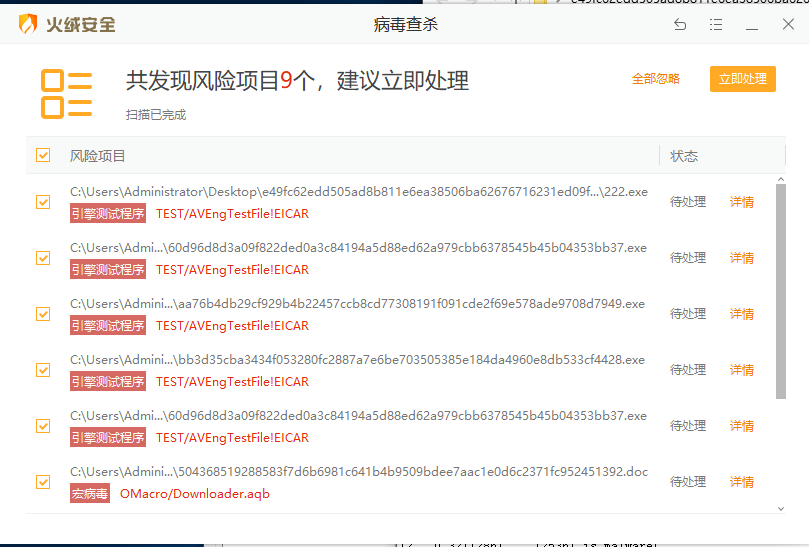 效果还是立竿见影,不错的 下一步准备给他接入yara和卡巴斯基的杀毒SDK... 阅读全文 2023-09-24 huoji 0 条评论
系统安全C/C++ [2018]在 Windows 10 上 WriteProcessMemory 比 NtWriteVirtualMemory 慢很多 WriteProcessMemory 不仅仅是一个NT包装函数,它还执行一些额外的工作(例如保护内存、刷新指令等) 通过逆向WPM 调用 NtQueryVirtualMemory 来确定我们正在写入的区域中页面的访问保护。如果访问保护不是正确的,WPM 将设置 ACCESS_VIOLATION 错误代码并返回(如果访问保护是 PAGE_NOACCES 或 PAGE_READONLY)。 如果没有,它会调用 NtProtectVirtualMemory 设置适当的访问保护。检查之后,函数调用 NtWriteVirtualMemory 和 NtFlushInstructionCache,对它们进行更多检查,然后返回。 这就是为什么慢的原因 阅读全文 2023-09-10 huoji 0 条评论
工具软件 [2023]安服专用的Chrome插件 2023.8.28: 超大更新 增加免费GPT接口,支持GPT带安全名词翻译(碾压其他的翻译,网络安全专业对口翻译) 支持GPT以安全研究员身份进行总结与介绍 UI更新 ksn云查:  新菜单:  安全总结:  专业翻译:  2023.8.27: 自己手搓的安服人员用的脚本,自动匹配MD5和SHA1并且进行KSN云查,需要去申请KSN密钥,地址: https://opentip.kaspersky.com/ 使用方法: 填了API密钥后,选中MD5、sha1、域名、ip即可进行IOC查询,可以查看流行度. 功能总览:  hash:  另外一个:  如果是病毒:  > GPT查询有数据敏感风险,请谨慎使用或者接入自己的本地GPT模型 更新: 支持GPT查询  油猴连接: https://greasyfork.org/zh-CN/scripts/474072 github https://github.com/huoji120/infosec_chrome_ext 阅读全文 2023-08-28 huoji 0 条评论
系统安全工具软件 [2023]通过GPT+词向量快速构造个人知识库 用的是llama_index这个项目,注意这个项目对embeding消耗贼大,谨慎使用 **!!!千万不要外网部署,因为这个项目存在已知的RCE和提示词注入问题** 这个llama_index的项目连接: https://github.com/jerryjliu/llama_index 这是部分效果(用了key08的资料+intel和amd手册): EAC:  免杀:  PG:  用我的代码,装好llama_index,然后把你的资料放在data目录就行.pdf、word、marketdown都可以 代码如下: 阅读全文 2023-07-31 huoji 0 条评论